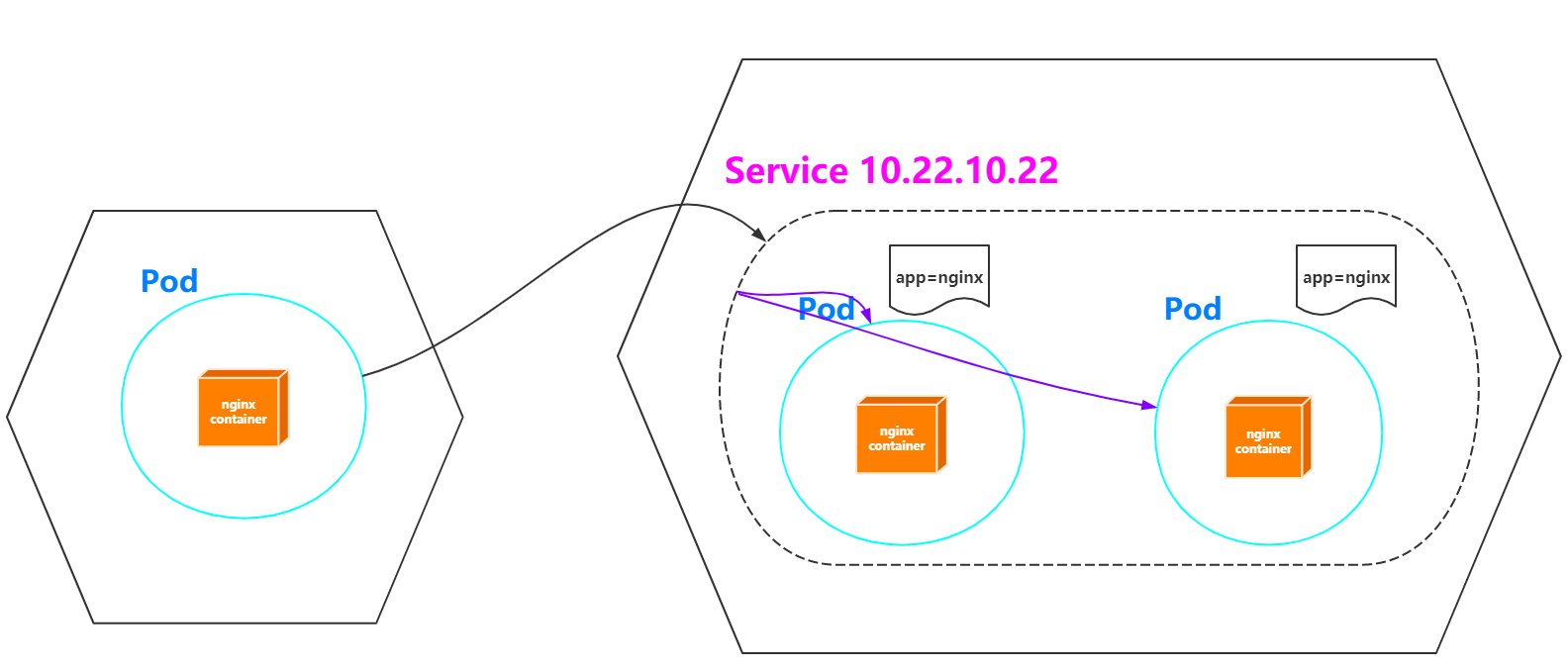
K8S Network Policy Allow Namespace . — first things first — use a network plugin that actually enforces network policies. — if you want to allow all connections from all pods in a namespace, you can create a policy that explicitly. This document helps you get started using the kubernetes networkpolicy api to declare. — a) to restrict access to both db pods from other namespaces. — to enable network policy enforcement when creating a new cluster, run the following command: — if you want to allow all traffic from all pods in a namespace (even if policies are added that cause some pods. specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints with an ip address in the block are allowed) how does. — declare network policy.
from blog.csdn.net
— first things first — use a network plugin that actually enforces network policies. — to enable network policy enforcement when creating a new cluster, run the following command: specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints with an ip address in the block are allowed) how does. — if you want to allow all traffic from all pods in a namespace (even if policies are added that cause some pods. This document helps you get started using the kubernetes networkpolicy api to declare. — if you want to allow all connections from all pods in a namespace, you can create a policy that explicitly. — a) to restrict access to both db pods from other namespaces. — declare network policy.
container namespacesCSDN博客
K8S Network Policy Allow Namespace — first things first — use a network plugin that actually enforces network policies. — declare network policy. — if you want to allow all connections from all pods in a namespace, you can create a policy that explicitly. — first things first — use a network plugin that actually enforces network policies. — a) to restrict access to both db pods from other namespaces. — if you want to allow all traffic from all pods in a namespace (even if policies are added that cause some pods. specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints with an ip address in the block are allowed) how does. This document helps you get started using the kubernetes networkpolicy api to declare. — to enable network policy enforcement when creating a new cluster, run the following command:
From zerojsh00.github.io
(K8S) 네트워크 Policy) 기초 개념 Simon's Research Center K8S Network Policy Allow Namespace — to enable network policy enforcement when creating a new cluster, run the following command: — if you want to allow all traffic from all pods in a namespace (even if policies are added that cause some pods. — a) to restrict access to both db pods from other namespaces. — declare network policy. —. K8S Network Policy Allow Namespace.
From blog.csdn.net
networkpolicyCSDN博客 K8S Network Policy Allow Namespace — if you want to allow all connections from all pods in a namespace, you can create a policy that explicitly. — declare network policy. — if you want to allow all traffic from all pods in a namespace (even if policies are added that cause some pods. specific namespaces (all pods in the namespace are. K8S Network Policy Allow Namespace.
From www.devopsschool.com
CKS What is Network Policy & Example Code K8S Network Policy Allow Namespace — first things first — use a network plugin that actually enforces network policies. — if you want to allow all connections from all pods in a namespace, you can create a policy that explicitly. specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints with an ip address in the block are allowed). K8S Network Policy Allow Namespace.
From blog.csdn.net
k8s network 配置protocolCSDN博客 K8S Network Policy Allow Namespace — first things first — use a network plugin that actually enforces network policies. — if you want to allow all traffic from all pods in a namespace (even if policies are added that cause some pods. This document helps you get started using the kubernetes networkpolicy api to declare. — declare network policy. — if. K8S Network Policy Allow Namespace.
From www.drupal.org
Manage K8s Network Policies [3093314] K8S Network Policy Allow Namespace This document helps you get started using the kubernetes networkpolicy api to declare. specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints with an ip address in the block are allowed) how does. — first things first — use a network plugin that actually enforces network policies. — declare network policy. —. K8S Network Policy Allow Namespace.
From marcuseddie.github.io
K8s network之一:K8s网络模型与网络策略 Mr.Muzi K8S Network Policy Allow Namespace — first things first — use a network plugin that actually enforces network policies. — declare network policy. — if you want to allow all connections from all pods in a namespace, you can create a policy that explicitly. — to enable network policy enforcement when creating a new cluster, run the following command: —. K8S Network Policy Allow Namespace.
From www.stacksimplify.com
Azure AKS Namespaces Introduction Azure Service K8S Network Policy Allow Namespace — if you want to allow all traffic from all pods in a namespace (even if policies are added that cause some pods. — if you want to allow all connections from all pods in a namespace, you can create a policy that explicitly. specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints. K8S Network Policy Allow Namespace.
From blog.csdn.net
K8S Network Policy Allow Namespace — to enable network policy enforcement when creating a new cluster, run the following command: This document helps you get started using the kubernetes networkpolicy api to declare. — a) to restrict access to both db pods from other namespaces. — if you want to allow all traffic from all pods in a namespace (even if policies. K8S Network Policy Allow Namespace.
From cilium.io
NetworkPolicy Editor Create, Visualize, and Share K8S Network Policy Allow Namespace — declare network policy. — to enable network policy enforcement when creating a new cluster, run the following command: — if you want to allow all traffic from all pods in a namespace (even if policies are added that cause some pods. This document helps you get started using the kubernetes networkpolicy api to declare. specific. K8S Network Policy Allow Namespace.
From cloud.tencent.com
部署k8s集群(k8s集群搭建详细实践版)腾讯云开发者社区腾讯云 K8S Network Policy Allow Namespace specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints with an ip address in the block are allowed) how does. — declare network policy. — first things first — use a network plugin that actually enforces network policies. — if you want to allow all traffic from all pods in a namespace. K8S Network Policy Allow Namespace.
From cilium.io
Network Policies Using Cilium Controlling Ingress/Egress K8S Network Policy Allow Namespace — a) to restrict access to both db pods from other namespaces. — declare network policy. — if you want to allow all connections from all pods in a namespace, you can create a policy that explicitly. — to enable network policy enforcement when creating a new cluster, run the following command: — if you. K8S Network Policy Allow Namespace.
From docs.cloud.f5.com
Create and Deploy Managed K8s F5 Distributed Cloud Tech Docs K8S Network Policy Allow Namespace — a) to restrict access to both db pods from other namespaces. — if you want to allow all connections from all pods in a namespace, you can create a policy that explicitly. — first things first — use a network plugin that actually enforces network policies. — to enable network policy enforcement when creating a. K8S Network Policy Allow Namespace.
From www.youtube.com
Network Policy Tutorial yaml explained + Demo Calico YouTube K8S Network Policy Allow Namespace specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints with an ip address in the block are allowed) how does. — if you want to allow all traffic from all pods in a namespace (even if policies are added that cause some pods. — a) to restrict access to both db pods from. K8S Network Policy Allow Namespace.
From blog.csdn.net
container namespacesCSDN博客 K8S Network Policy Allow Namespace — a) to restrict access to both db pods from other namespaces. — first things first — use a network plugin that actually enforces network policies. This document helps you get started using the kubernetes networkpolicy api to declare. specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints with an ip address in. K8S Network Policy Allow Namespace.
From akash-zade.hashnode.dev
Namespaces and Services in K8s K8S Network Policy Allow Namespace — first things first — use a network plugin that actually enforces network policies. specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints with an ip address in the block are allowed) how does. — if you want to allow all traffic from all pods in a namespace (even if policies are added. K8S Network Policy Allow Namespace.
From www.bilibili.com
理解K8s的Namespace和KubeDns 哔哩哔哩 K8S Network Policy Allow Namespace specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints with an ip address in the block are allowed) how does. — first things first — use a network plugin that actually enforces network policies. — to enable network policy enforcement when creating a new cluster, run the following command: — if you. K8S Network Policy Allow Namespace.
From heffenvox.com
How to access your K8s cluster apps K8s’ network 101 Heffen Vox K8S Network Policy Allow Namespace This document helps you get started using the kubernetes networkpolicy api to declare. — if you want to allow all connections from all pods in a namespace, you can create a policy that explicitly. specific namespaces (all pods in the namespace are allowed) ip address blocks (endpoints with an ip address in the block are allowed) how does.. K8S Network Policy Allow Namespace.
From medium.com
— Day 6 k8s Namespaces and RBAC!! by Navya Cloudops Medium K8S Network Policy Allow Namespace — a) to restrict access to both db pods from other namespaces. — if you want to allow all connections from all pods in a namespace, you can create a policy that explicitly. — if you want to allow all traffic from all pods in a namespace (even if policies are added that cause some pods. This. K8S Network Policy Allow Namespace.